Employees spot security anomalies every day, but critical observations evaporate
Cybersecurity isn’t just about technology—it’s about people. Every day, employees come across odd activity, from craftily disguised phishing emails and texts, to suspicious behavior on-site. These frontline observers can be a company’s strongest defense, yet, without a scalable approach to turn observations into strategic data, vulnerabilities remain unaddressed. That’s where the Groopit Cyber Security Solution comes in.
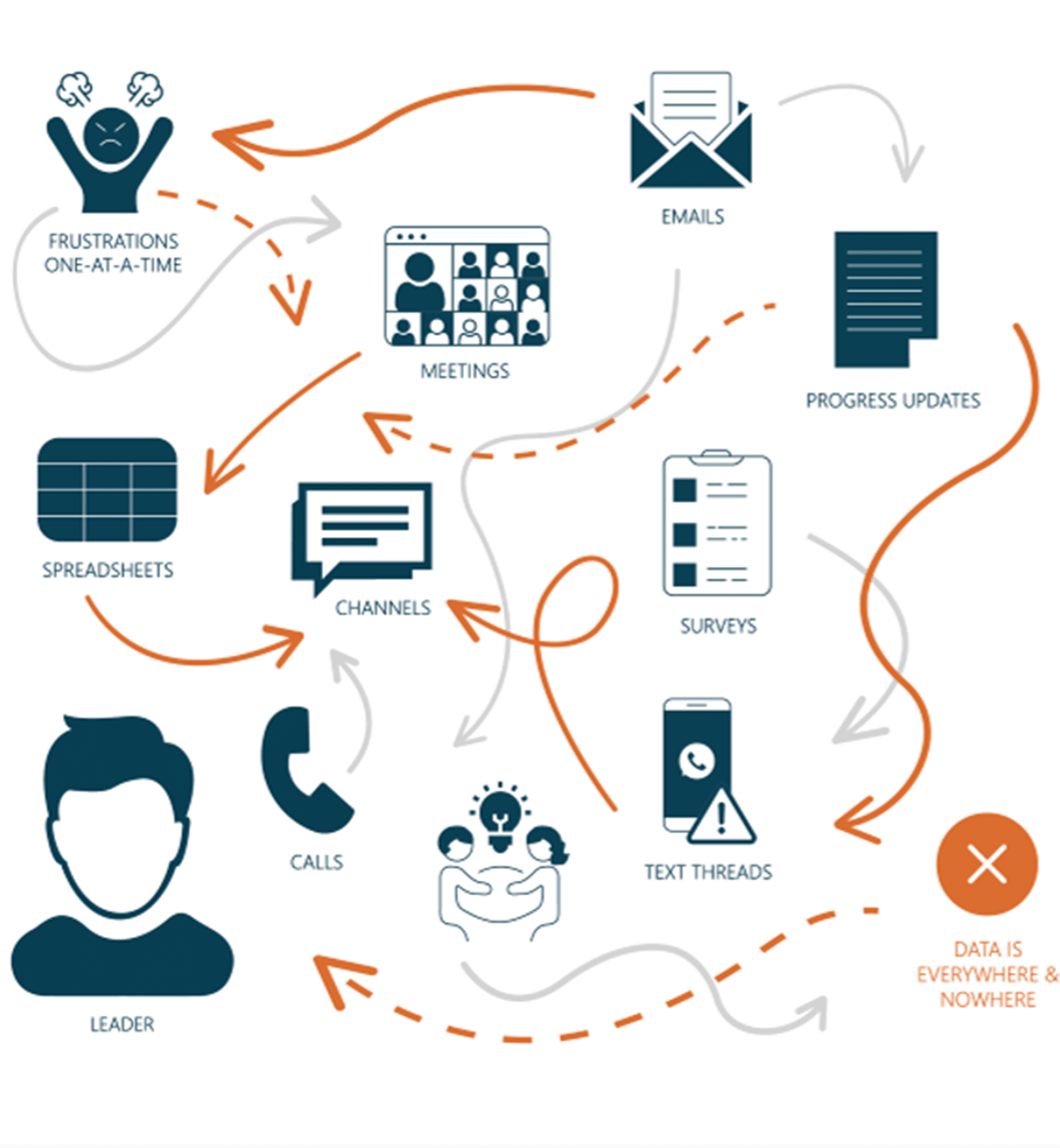

The Groopit Cyber Security Intelligence Solution radically simplifies how companies get and use intel from employees for enterprise security.
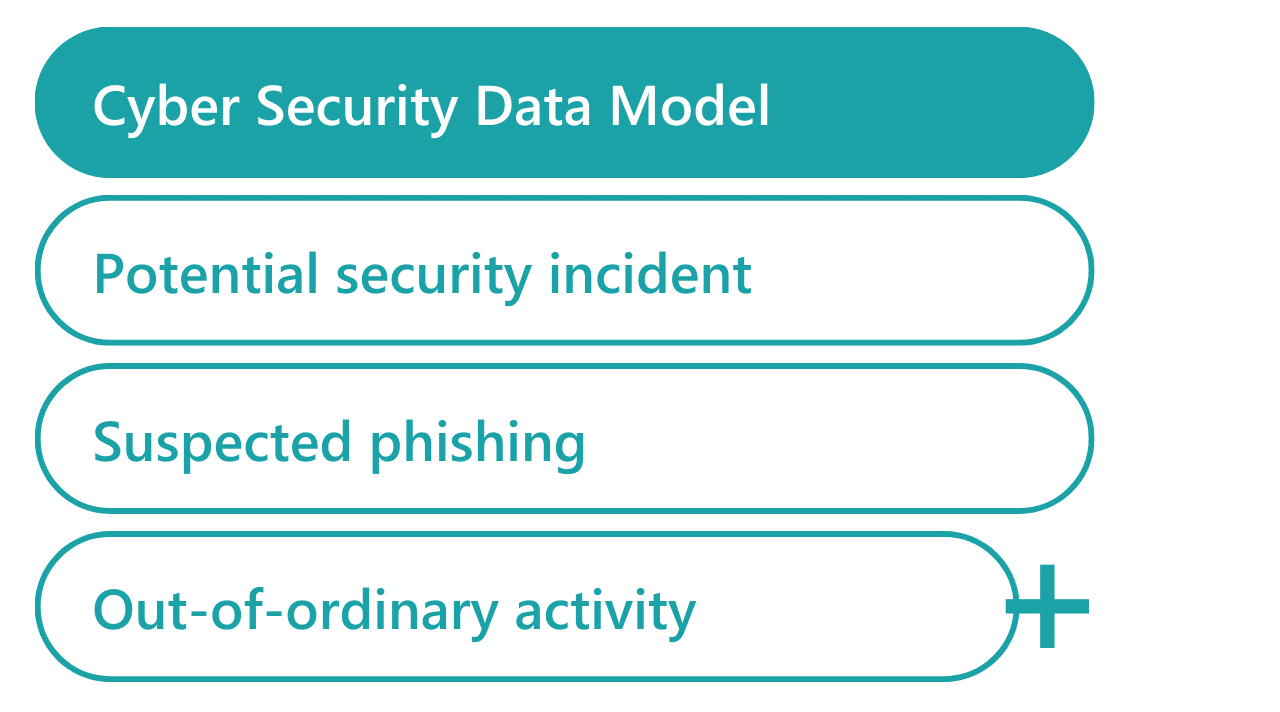
Tap into employee insights with a data model
With Groopit, you’ll bridge the gap between employee vigilance and fortified enterprise security by establishing an underlying data model for employee generated insights about cyber security.
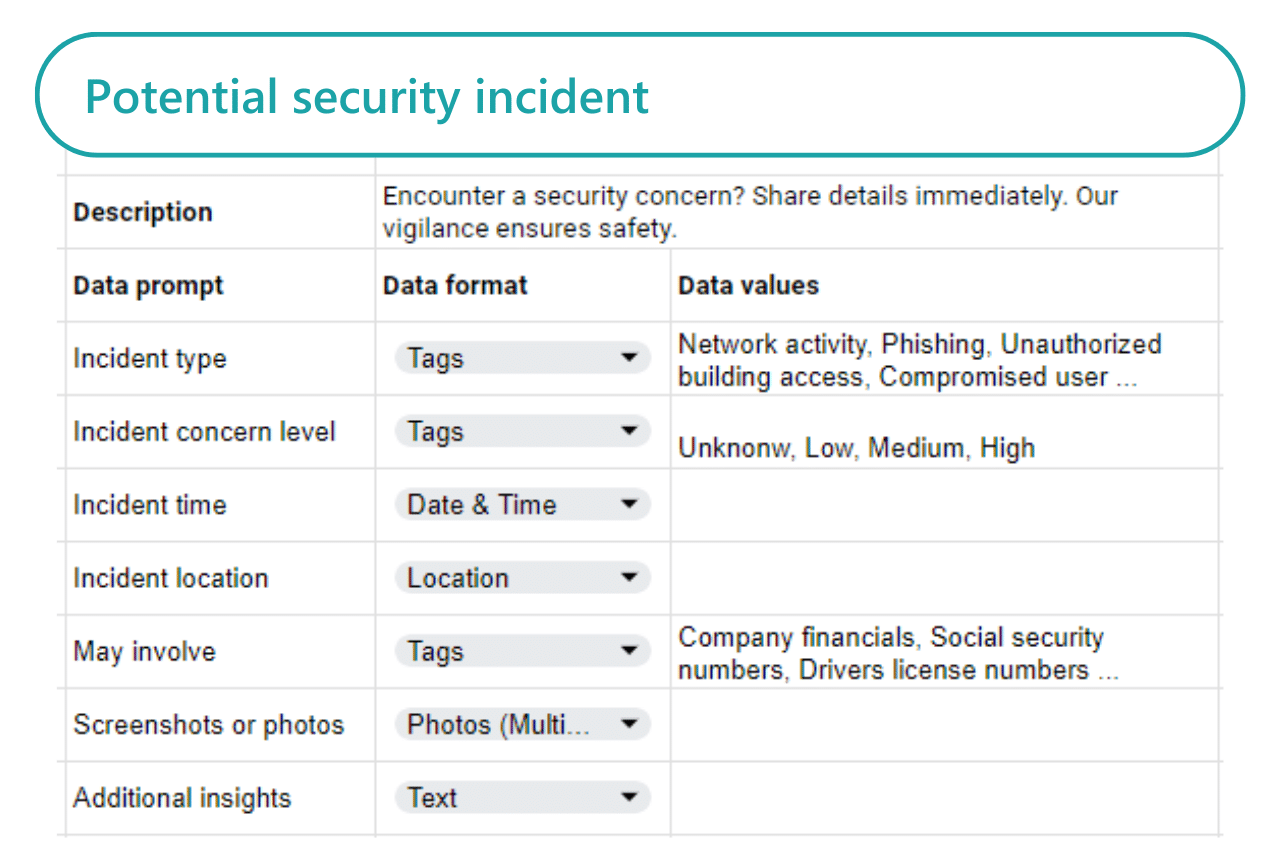
Operate with agility and speed
Need increased vigilance on a new threat or to deep dive on a new topic? No problem. Groopit makes it easy to adjust the data model on-the-fly. Start from scratch or with a template, and move fast. You control the intel people share across enterprise systems.
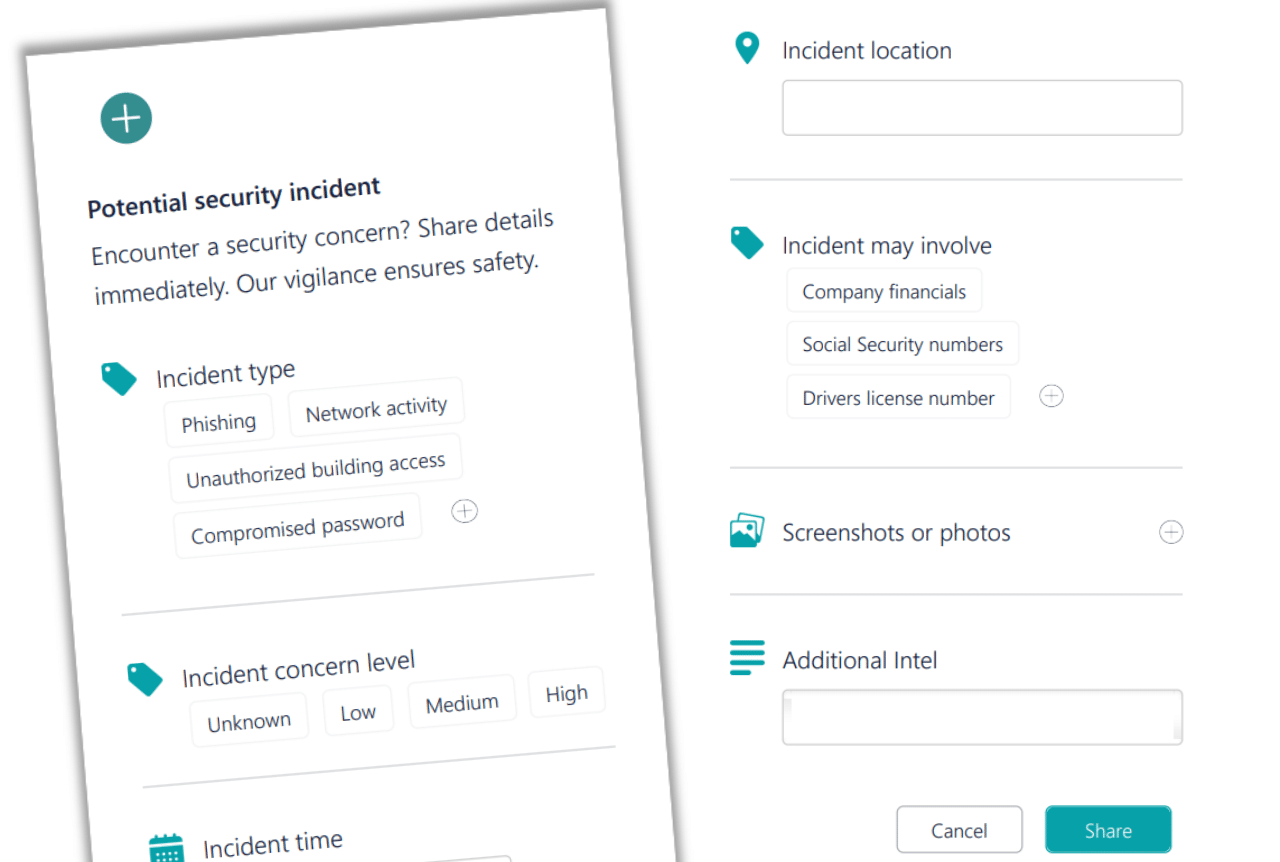
Radically simplify sharing of cyber security intelligence
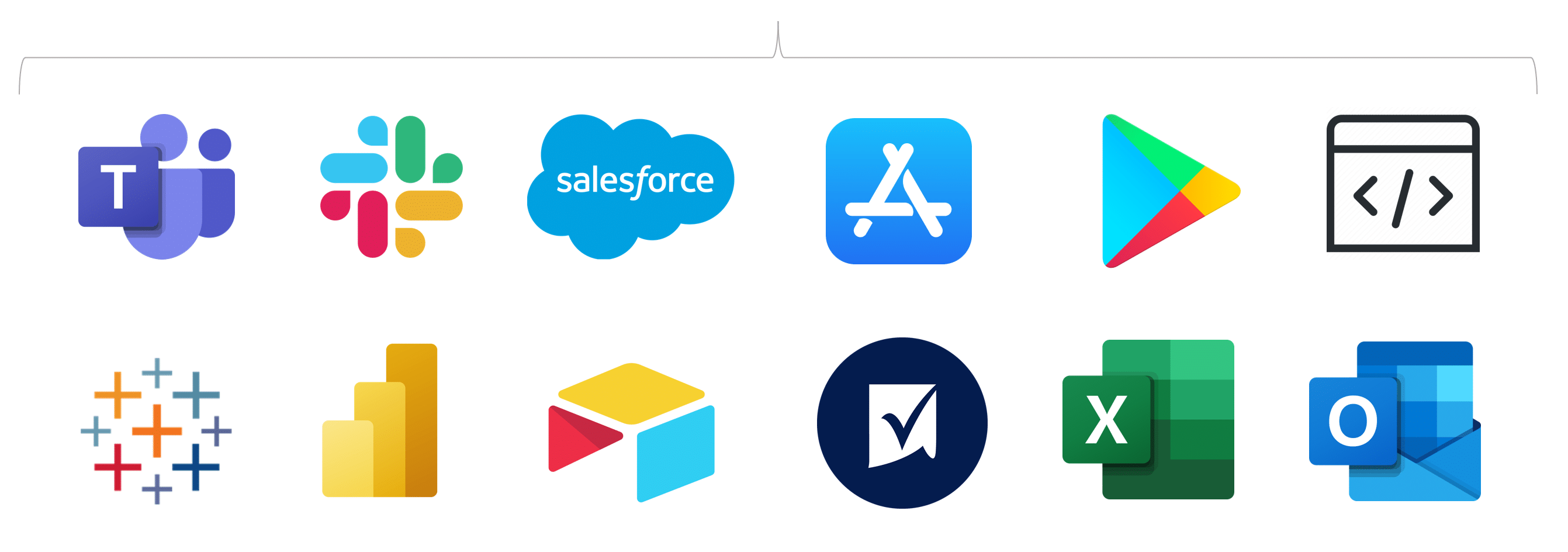
With Groopit, employees share intel in 3 taps or less than 1 minute, from where they already work: Teams, Slack, Salesforce, mobile apps, and more. Groopit removes all the friction so employees share what they know.
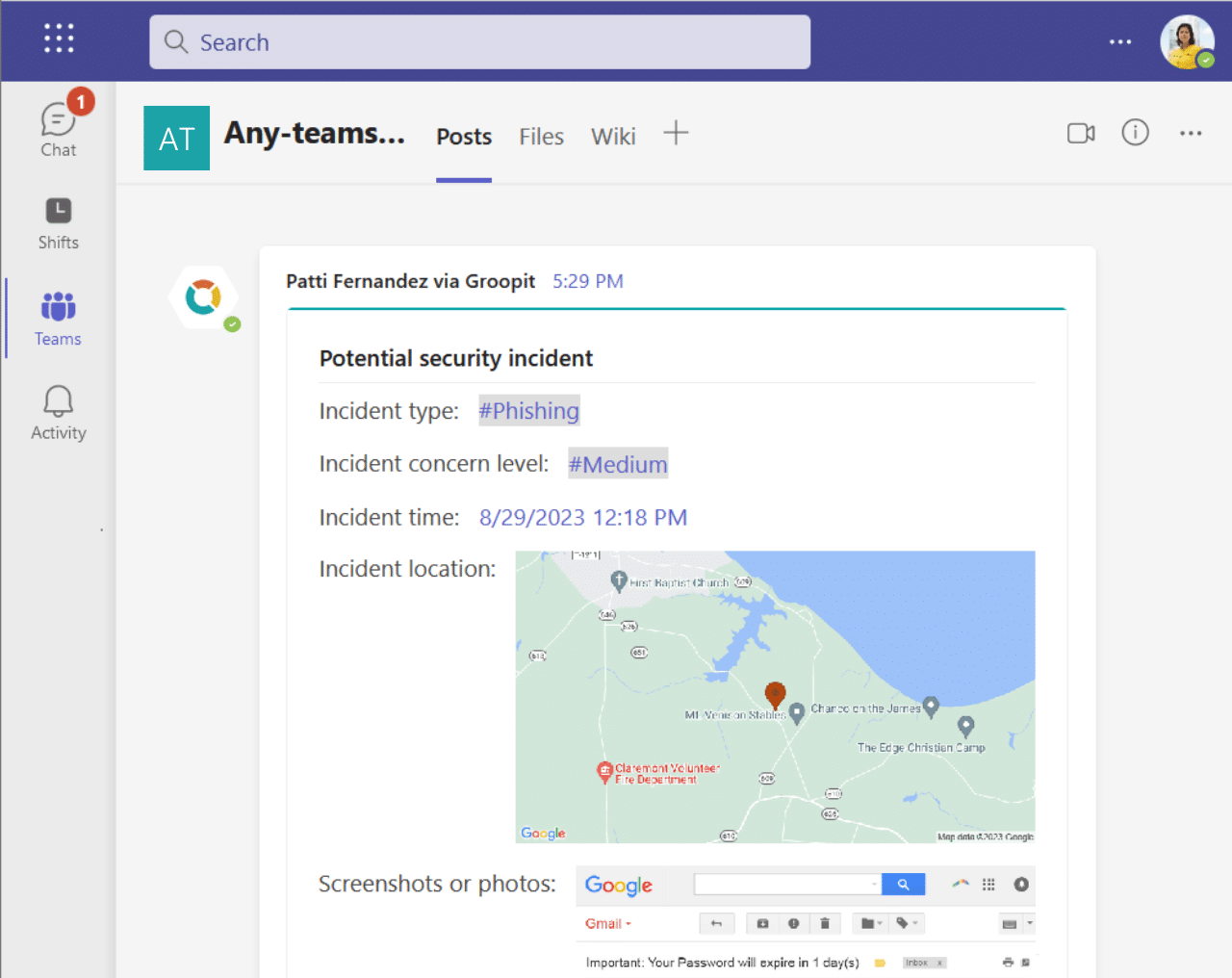
Deliver cyber security intel directly to analysts
The Groopit Cyber Security Intelligence Solution aggregates and delivers intel to the appropriate analysts. Physical security issues delivered to appropriate regional or local teams, phishing activity delivered to key analysts, and so on. For the first time, a company’s collective intel can be leveraged across disciplines.
“This is a data-oriented solution to turn employee observations about security into data our security team can monitor and act upon.”
“
Groopit Customer