Get your team setup and connected with Microsoft Entra ID (formerly known as Azure AD) in Groopit. This guide will walk you through the supported features, requirements and configuration steps.
Supported Features
- Single Sign-On via OpenID Connect (OIDC)
- Provisioning users and groups with SCIM (optional)
Requirements
- Your Groopit organization must be part of an organization with an active Groopit Enterprise Subscription
- An Entra user account with one of the following roles: Global Administrator, Cloud Application Administrator, or Application Administrator
SSO Configuration Steps
- Install the Groopit application within your Entra Tenant (Link)
If you are logged in with an Entra admin account, you will be presented with the “Admin consent” dialog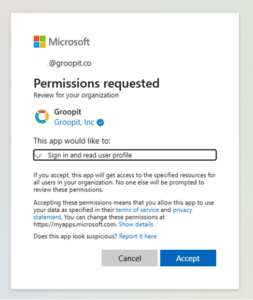
2. After granting the requested permissions, Entra configuration is complete. Contact your Groopit customer success representative to enable SSO for the Groopit application.
Once setup is complete users will be required to use SSO to sign-in to Groopit.
SCIM Configuration Steps (optional)
If you are planning to use Entra security groups to control access to Groopit groups, the use of SCIM (System for Cross-domain Identity Management) is recommended. Groopit provides a SCIM-compliant endpoint, but it must be manually added to the Entra tenant to enable SCIM provisioning. The first part of this process must be performed by the tenant administrator in the Groopit application.

For more information on privacy, please review our Privacy Policy.